Digital transformation is a fact, and several companies have transferred their IT operations to the cloud. In conjunction with the move to the cloud, IT operations are commonly insourced. This creates several advantages, where scalability and agile work are the main driving forces.
Insourcing IT operations means someone at the company administrates the app portfolio. You must keep track of; who has access to each service and design and who should be granted access when onboarding. It can be challenging to track who purchases digital services, systems, and cloud-based services from various departments. On top of it all, you are expected to keep track of costs, renewal dates, and when licenses expire.
No longer solely the IT department that purchases digital services
In the past, most went through the IT department. But today, IT purchases are made from other parts of the organization to an increasing extent. We know what we want and need to improve our work efficiency. We quickly want to find what is best suitable for us and helps us with specific tasks.
When IT bears the exclusive administrative burden for managing all digital services within the company, success becomes challenging as IT no longer holds all the puzzle pieces. Suppose you are unaware of what is purchased and by whom. Then the problem arises that services fly “under the radar,” i.e., shadow-IT.

Security is essential
Safety is a driving factor in moving services to the cloud. From a security perspective, it’s essential to administrate all service users in order to gain internal control. This applies to paid services and all free services available at the company, as this is where the company’s data is stored. Here is where offboarding becomes essential.
Picture a company with 100 employees and 50 subscriptions. Sounds manageable, right? But when we look at how many connections exist between users and services in the core business, the company has 5,000 unique user accounts to administer — the bigger the company, the more links.
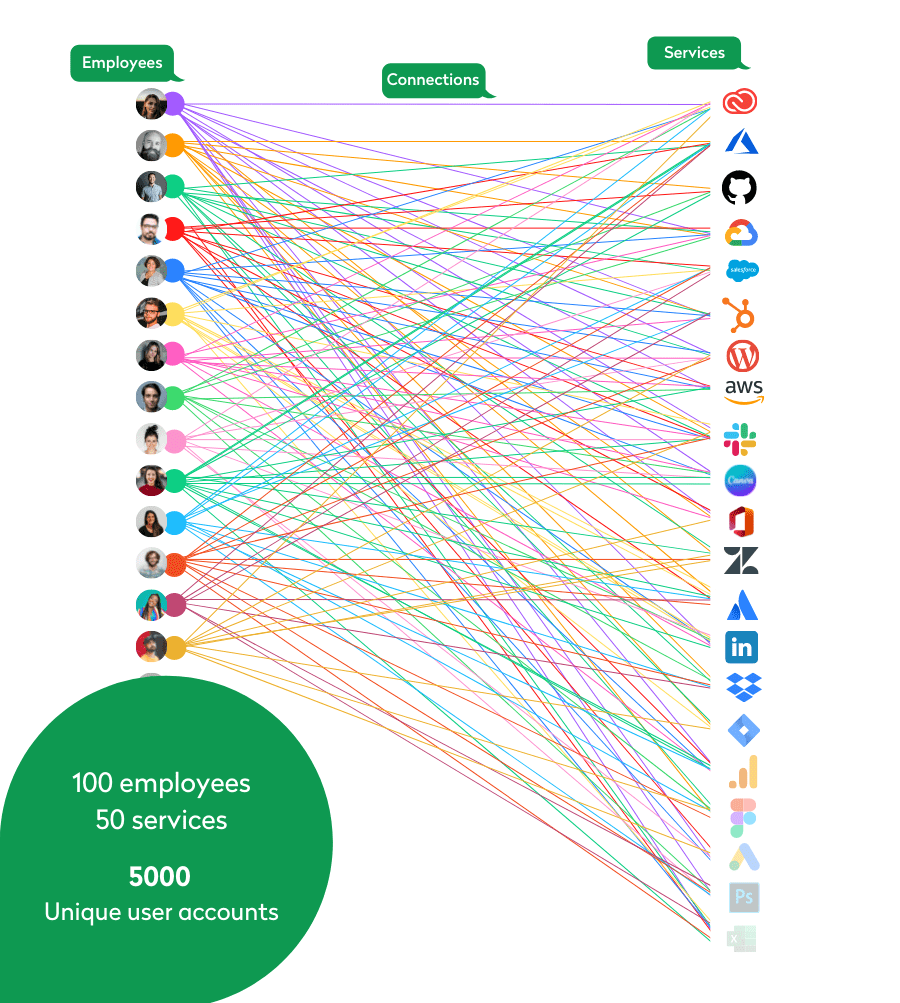
Each connection must be handled properly to ensure unauthorized people don’t have access to company data. Here it is necessary to have a clear and structured offboarding process. Every service an employee had access to must be deactivated to shut the door and not risk any security breaches. At the same time, ensure that the company does not pay for services that are not being used.
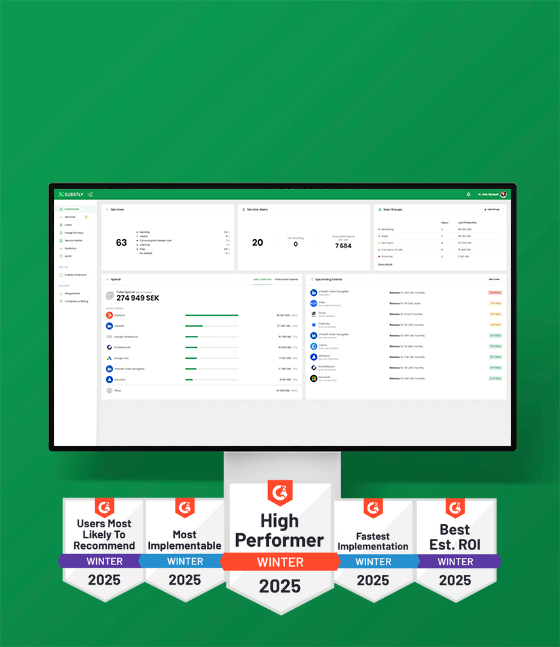
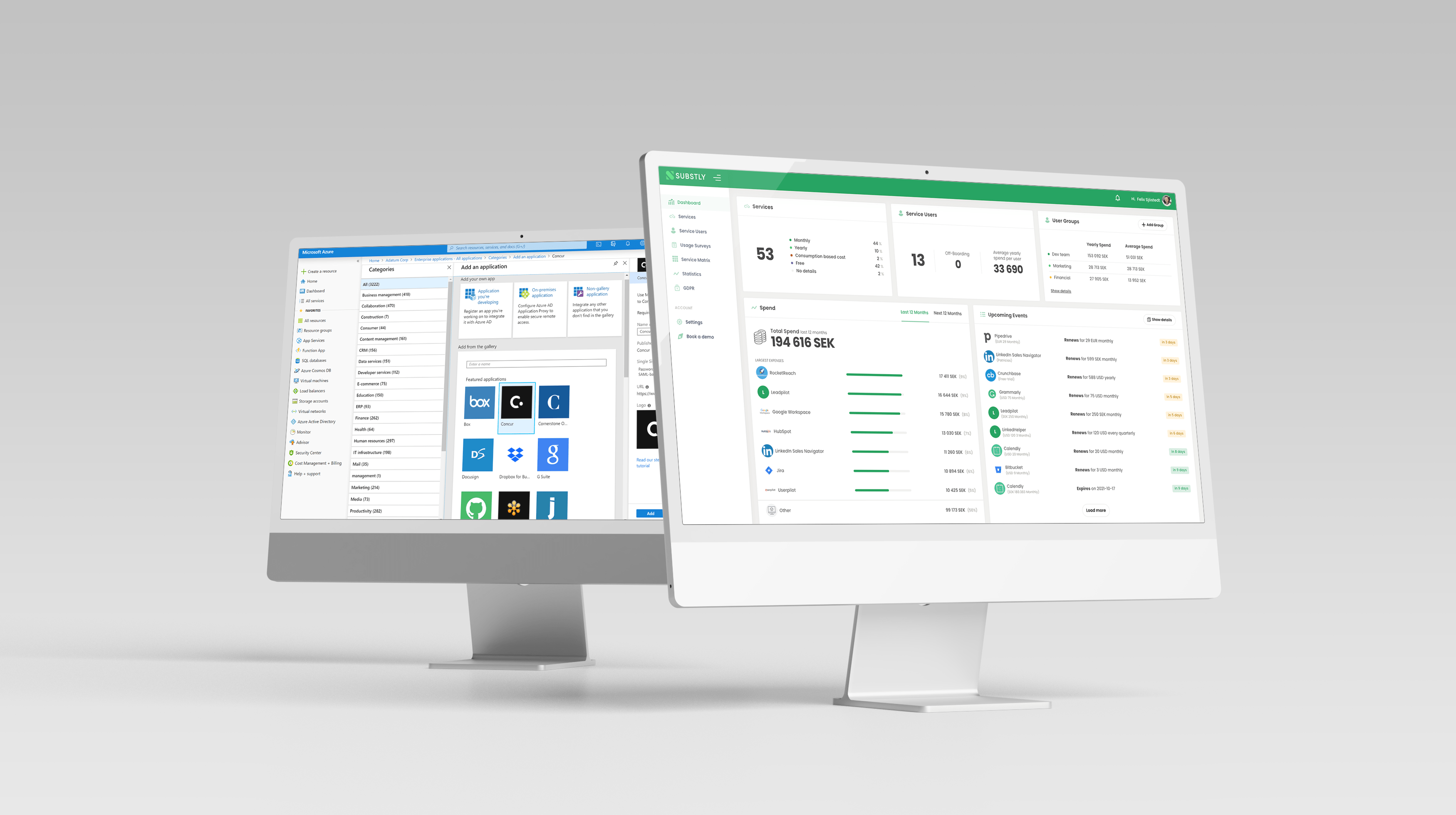
Some solutions may facilitate your management and simplify your everyday life if you utilize an insourced model of your IT operations. Substly offers such a service, and ensures that your IT department can follow all SaaS management best practices with ease.
Substly helps you get a complete overview of your digital services, what they cost, and who has access to what. In addition, you can invite other administrators to work alongside you, as well as categorize software between different internal teams. This collaboration saves time and opens up more transparent mutual communication across departments, potential cost savings, risk assessment, and better data-driven decisions.
Related articles
SaaS Management: What is it, tips for getting started & best practices
SaaS management for CTOs; Increase Security and Save Money
Managing the Risks of SaaS Sprawl and Shadow IT